M01 Introduction to Data Networks
Lecture Videos
What is the Internet?
Internet is The Network ... of all networks.
And as such it needs governance, standardization and agreements.
Governance
IANA - Internet Assigned Numbers Authority
The top notch society of the Internet. This doesn't mean it can dictate things in the Internet, but act as a remidiator.
Quote: https://www.iana.org/numbers
We are responsible for global coordination of the Internet Protocol addressing systems, as well as the Autonomous System Numbers used for routing Internet traffic.
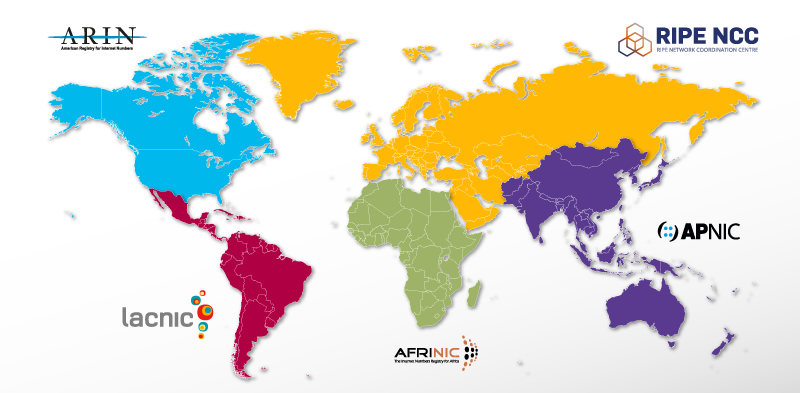
IANA consists of multple Regional Internet Registeries called RIR's. They are geographically distributed in the world.
Quote: Picture from https://ripe.net
| Registry | Area Covered |
|---|---|
| AFRINIC | Africa Region |
| APNIC | Asia/Pacific Region |
| ARIN | Canada, USA, and some Caribbean Islands |
| LACNIC | Latin America and some Caribbean Islands |
| RIPE NCC | Europe, the Middle East, and Central Asia |
As in Finland, we are a part of RIPE's area and RIPE offers a list of Local Internet Registries called LIR's as a list of its members.
Standardization
IETF - Internet Engineering Task Force
Quote: https://www.ietf.org/about/
The IETF is a large open international community of network designers, operators, vendors, and researchers concerned with the evolution of the Internet architecture and the smooth operation of the Internet.
IETF publishes Requests for Comments (RFCs) which are considered as standards of the Internet. One of the most notable would be e.g. RFC 791 - Internet Protocol.
IEEE - Institute of Electrical and Electronics Engineers
Quote: https://www.ieee.org/about
IEEE and its members inspire a global community to innovate for a better tomorrow through its more than 419,000 members in over 160 countries, and its highly cited publications, conferences, technology standards, and professional and educational activities. IEEE is the trusted “voice” for engineering, computing, and technology information around the globe.
IEEE publishes standards such as
- IEEE 802.11 (wireless Ethernet)
- IEEE 802.1 through 802.3 (wired Ethernet)
ISP - Internet Service Providers
ISPs - are the companies that provide you access to the Internet. They sell you the (internet) connection and take care of the rest.
Something to note is that the Internet is mostly ran by private companies.
As it is a highway to the Internet, think if the actual road highway next to you was owned by an private company?
Charging for your (road) connection to it and car travels per month.
Similarly to how many packets of data you send.
How about charges per kilogram you transfer cargo through that road?
How many bytes are you sending per packet?
ISPs are distributed (unofficially) into Tiers 1 to 3, based on their dependance of each other to transmit data.
Tier 1
Tier 1 can handle traffic throughout an continent or several.
- Telia (Carrier)
- Verizon
- AT&T
Tier 2
Tier 2 can function in several countries.
- Elisa
- Orange
Tier 3
Tier 3 ISPs typically handle customer connection to their core at a regional area offering 'close to the customer' services that larger corporations struggle to achieve.
Internet eXchange Points - IXP
Internet service providers are connected to one another through physical locations where devices from different ISPs connect to one another and form routing neighborships (peers / peering) to exchange routing information.
Finnish Communication and Internet Exchange association (FICIX) is one of the largest IXP in Finland.
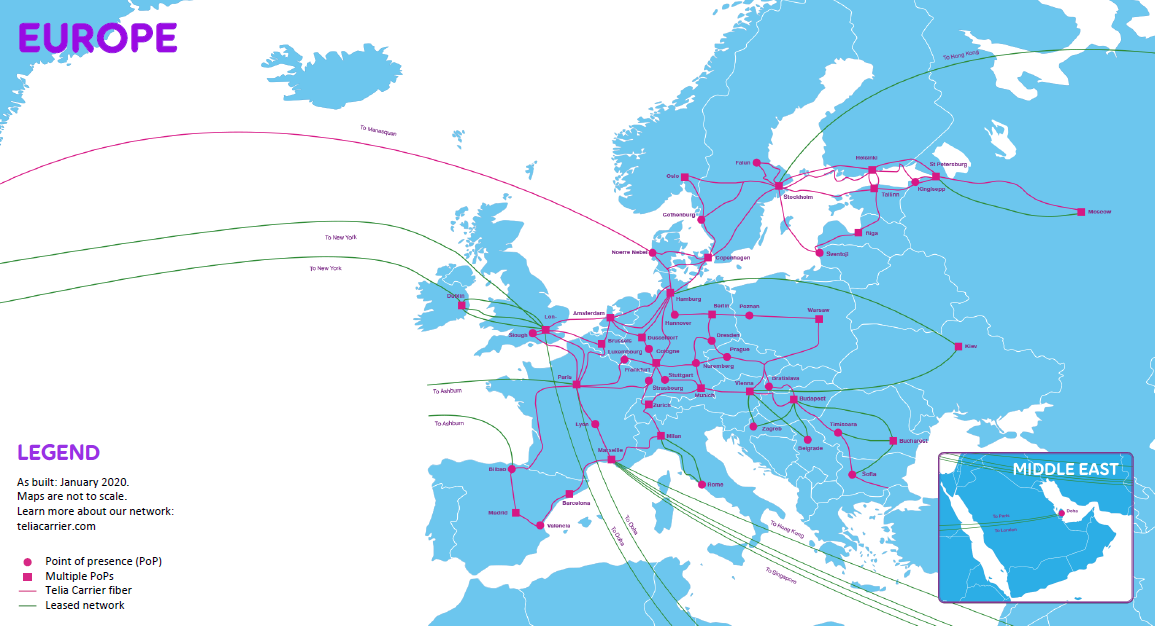
Points of Presence - PoP
PoPs are a way to establish presence of a geographical area. This means an office or distribution center of connections is established. Depending on the geographical legislation, the responsibility of the ISP ends or starts here.
Quote: Picture of Telia Carrier PoPs, https://www.teliacarrier.com/our-network.html
Quote: Links to FUNET (Finnish University NETwork) network maps
Air-gapped networks
Not everything is connected to the Internet.
It is good to know that there are networks, that don't want to connect to other networks. These are usually thought of "Air-gapped Networks" that handle data that might be considered classified.
Examples of these networks would be:
- Industrial Control Systems
- Nuclear Power Plants
- Government Networks
- Public Authority Networks (e.g. Police)
- Military Networks
- Transportation Networks
- Train traffic
- Aviation
- Automotive
- Marine traffic
Background of Data Networks
Video: Data Networks, Introduction to Data Networks, part 2
Communication is an integral part of society. Lives have been lost because a message couldn't get through. Battles and Wars have started because of bad communication.
History cannot be neglegted while learning where we are now.
Data Networks have been developed throughout the ages to respond to this need to communicate between people. Be it letter transmitting postal office networks to computer networks.
- Data is at the core of this need to hand it over to one another
- Networks respond to this need to provide a solution on how to get the data across
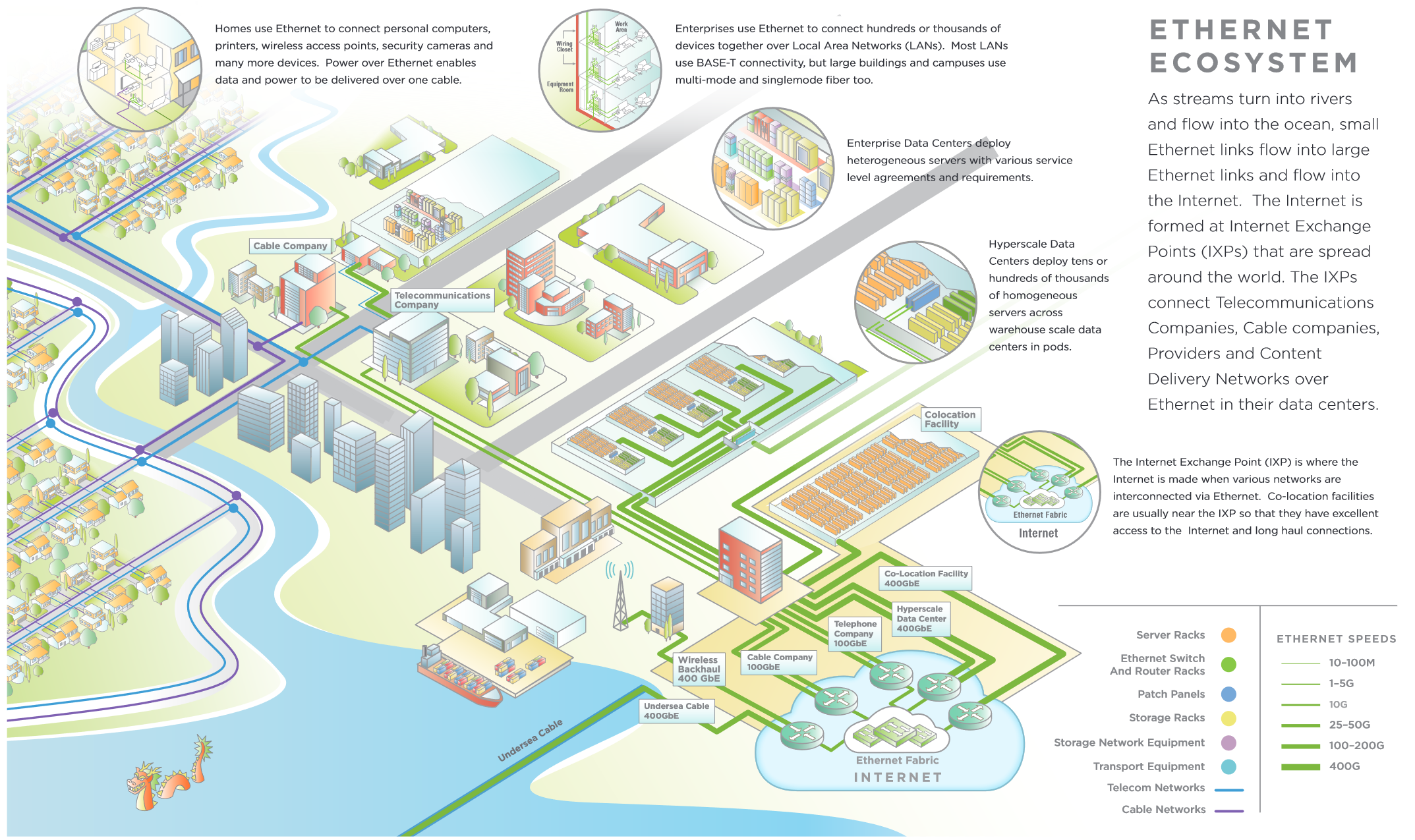
One visualization of our society would be through this image. Think of all the different organizations, personel and devices using a network by looking at the picture.
Quote: Picture from Ethernet 2020 Roadmap, Ethernet Alliance
What is Data?
The Background
The air pressure variations that our vocal cords produce is one way of transmitting data. Smoke signals produced from a fire could be one way of transmitting data through visible light (through the Electromagnetic Spectrum).
Sensors measure these phenomenons in physics and turn them into electricity voltage. Which in turn can be read by electronics, and changed into bits. Types of sensors are:
- Dynamic Microphone / Moving Coil Microphone (sound)
- Phototransistor (light)
- Thermistor (temperature)
Typically Internet of Things (or IoT) devices contain these measurement sensors. They read environment data, transform it into bits and then transmit the information into the network.
Data in the computer age
To hastely come to this day and age, Data Networks today are about 1s and 0s (the bits). The language of the computers, that is known as binary. Typically in electronics, these 1s and 0s are either voltage ON (e.g. +5V) or voltage OFF (ground or 0V).
Binary
Typically we have assigned meaning to the 1s and 0s:
| Value as Binary | Meaning |
|---|---|
| 0 | False |
| 1 | True |
A series of 8 bits is called a byte e.g. 0100 0001.
ASCII -formatting
As computers were developed, the letters of the alphabet were designed to be represented by 8 bits (or 1 byte). Thus the term byte stuck, eventhough people often confuse if they are talking about bits or bytes.
If we go to more specific assignments e.g. the ASCII -formatting of text:
| Value as Binary | Meaning |
|---|---|
| 0100 0001 | A |
| 0100 0010 | B |
| 0100 0011 | C |
| ... | ... |
| 0110 0001 | a |
| 0110 0010 | b |
| 0110 0011 | c |
How many bytes have I used?
For common people it is hard to explain how many kilobits have they used of their mobile connection. Or what are the differences between bits or bytes. "Digital Technology and Hardware" course concentrates more on these topics, but to quickly summarize:
- one letter of the alphabet = 8 bits = 1 byte
- 140 letter text message (from phones) = 140 letters * 8 bits =
- 1120 bits = 1,12 kilobits
- 140 bytes = 0,14 kilobytes
Bits use the same metric system (or metric prefix/unit prefix) as physics, thus the most commonly used in IT:
| prefix | symbol | Base10 | Decimal | name |
|---|---|---|---|---|
| tera | T | 10^12 | 1 000 000 000 000 | trillion |
| giga | G | 10^9 | 1 000 000 000 | billion |
| mega | M | 10^6 | 1 000 000 | million |
| kilo | k | 10^3 | 1 000 | thousand |
| bit | b | 1 | 1 | one |
Because binary is a power of 2 system the chart is actually
| prefix | symbol | Base2 | Decimal | name |
|---|---|---|---|---|
| tera | T | 2^40 | 1 099 511 627 776 | terabits |
| giga | G | 2^30 | 1 073 741 824 | gigabits |
| mega | M | 2^20 | 1 048 576 | megabits |
| kilo | k | 2^10 | 1 024 | kilobits |
| bit | b | 1 | 1 | bit |
You can ask more about these in Mathematics courses
The Speed of Transmission
The letter is formed by transmitting 8 bits (8 x 1s or 0s) also known as a byte.
A transmission rate of 8 bit/second would mean that 1 seconds of time would take to pass through one letter. This speed of data transmission can be represented in many ways:
- 8 b/s
- 8 bps
But as stated this might also be represented by 1 byte / second:
- 1 B/s
- 1 kB/s
- 1 MB/s
- 1 Bps
A Network Engineer should know the difference between 100 Mb/s and 100 MB/s
Quite often different software print out different speeds.
Networks are typically measured through how many bits per second they can transmit.
But with files (and their transfer speed) the programmers like to use bytes per second.
Various other representations of data
Hexadecimal
Hexadecimals are a shorter way to represent bits. As simply put it we have symbols for each different 4 bit row.
| Decimal - dec | Binary - bin | Hexadecimal - hex |
|---|---|---|
| 0 | 0000 | 0 |
| 1 | 0001 | 1 |
| 2 | 0010 | 2 |
| 3 | 0011 | 3 |
| 4 | 0100 | 4 |
| 5 | 0101 | 5 |
| 6 | 0110 | 6 |
| 7 | 0111 | 7 |
| 8 | 1000 | 8 |
| 9 | 1001 | 9 |
| 10 | 1010 | a |
| 11 | 1011 | b |
| 12 | 1100 | c |
| 13 | 1101 | d |
| 14 | 1110 | e |
| 15 | 1111 | f |
Example of reading a file in hexadecimal on Linux
-bash-4.1$ hexdump -C text.txt
00000000 41 42 43 61 62 63 0a |ABCabc.|
41 hex, where
4 hex = 0100 bin
1 hex = 0001 bin
41 hex = 0100 0001 bin = A (letter in ASCII)
How to write Karo Saharinen in ASCII/HEX/BIN?
Karo Saharinen
4b 61 72 6f 20 53 61 68 61 72 69 6e 65 6e
01001011 01100001 01110010 01101111 00100000 01010011 01100001 01101000 01100001 01110010 01101001 01101110 01100101 01101110
Encodings for Writing
Note that ASCII is a very limited representation of data. Multiple different encoding mechanisms are used in the world.
- UTF-8
- UTF-16
- UTF-32
- Unicode
- BASE64
Want to try out conversions? Try CyberChef
There is a lot of them :)
What are Networks?
The Background
To trace back to history...
The first basic networks of data transmission were formed e.g. in forests through the atmosphere. If no visible line of sight between hunters can be formed, one way to stay on track where everyone is, ... is to shout to one another. This can transmit the data of location and e.g. direction or sightings of game.
Smoke signals are one way to get the message across. This means there is a requirement of line of sight, between the transmission participants.
Warfare and other needs have developed this line of sight to a Optical Telegraph. This method of transmitting letters or words through signs over far distances was most widely used in France in the 1800th century.
With the invention of electricity, Morse coding and the Electrical Telegraph was introduced to mankind. Placing an electric current on (true) and off (false) was an efficient way to get the message farther than line of sight.
Electrical Telegraph brought the need of building a electrical conduit between transmission participants. Thus very long copper cables between cities were built.
Telegraphs in Finland, Yle Elävä arkisto
The video above is ... a product of its time. And this is why it is in the archives of Yle.
Networks in the computer age
As the Internet is everywhere, typically it is categorized into the following categories.
Personal Area Networks - PAN
Typically these networks range from 0.1 meters to 10 meters, but often not further. In wireless, they support low bandwidth data transfer and usually connect consumer electronics to one another.
Examples of PAN networks:
- Wireless
- Bluetooth
- Mouse, keyboard, headset and other personal accessories
- Zigbee
- House Lights (Philips Hue)
- Bluetooth
- Wired
- USB
- FireWire
Local Area Networks - LAN
The range of LANs usually is around 1 meters to 200 meters. They encompass buildings and connect end devices (e.g. workstations) to a data network.
Examples of LAN networks:
- Wireless
- WLANs (802.11)
- Wired
- Wired Ethernet (802.3)
- Coaxial networks (e.g. TV transmission)
Metro Area Networks - MAN
MAN networks, which range from 100 meters to 80 kilometers, might be more unfamiliar to the consumer. But usually they are the way to connect consumers and businesses into the larger "Core/WAN Network". Thus as an connection method these are sold to consumers also.
Examples of MAN networks:
- Wireless
- 2G/3G/4G/5G "telephone networks"
- Wired
- MetroEthernet
- Coarse Wavelength Division Multiplexing
- xDSL -connections (e.g. ADSL)
- (euro)DOCSIS networks (cable TV -networks)
Wide Area Networks - WAN
The "Core Networks" or Wide Area Networks are the stuff of Internet Service Providers (ISPs). This is where the big guns are in data networks as they range from 80 kilometers to ... basically undersea cables with lengths up to 39 000 kilometers.
Quote: Map of the Longest undersea SEA-ME-WE 3 cable - Submarinenetworks.com
Examples of WAN networks:
- Wireless
- LoRaWAN
- NB-IoT
- Wired
- Dense Wavelength Division Multiplexing (DWDM)
- MPLS-VPN Networks
- Optical Transport Networks (OTNs)
- Synchronous Digital Hierarchy (SDH)
Making communication structured
Video: Data Networks, Introduction to Data Networks, part 3
Through the invention of computers, the need for standardisation came evident to increase compatibility between countries and continents. There are many cases in history where different networks were incompatible and meant huge costs for consumers to make e.g. long-distance calls.
These days are now gone by, but that was helped by the most notorious models of standardization:
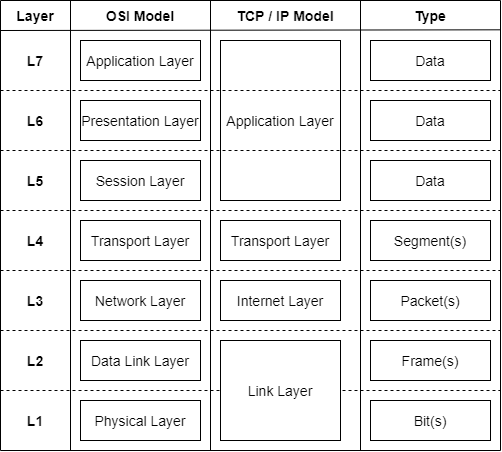
- The OSI Model
- the TCP / IP Model.
These models MUST be known by every engineer in the field of IT
The Big Picture
The OSI Model
Layer 1 - Physical Layer
The Physical Layer handles bits. Be these bits photons or electrons, they are usually transmitted through fiber cables or copper cables. This means that modulation and amplitude have to be taken into account on the physical layer. Also the connectors that connect the cables are usually defined.
- Connectors
- RJ-45
- LC
- SC
- Cables
- Single-mode Fiber
- CAT5 cable
- Coaxial cables
- Modulations
- Non-Return to Zero (NRZ)
- Manchester
- QAM256 (Quadrant Amplitude Modulation 256 bit)
Layer 2 - Data Link Layer
The Data Link layer takes these bits and starts to form frames. Frames, their fields and lenghts, have been agreed upon in standards. These frame formats can be:
- Ethernet
- OTN
- SDH
- ATM
- Frame-relay
- X.25
Layer 3 - Network Layer
The Network Layer takes care of packets. The packets usually only have a header. Most known packet formats are:
- Internet Protocol
- Version 4 (IPv4)
- Version 6 (IPv6)
But others do exist:
- CLNP
- IPX
- AppleTalk
Layer 4 - Transport Layer
The Transport Layer takes care of segments. Typically to make sure that data is received in the correct order, and if necessary, retransmitted through the network. Protocols on this layer:
- Transmission Control Protocol (TCP)
- User Datagram Protocol (UDP)
Layer 5 - Session Layer
The Session Layer is something that is quite often missing in the TCP/IP -model. Thus the protocols might be less known, but still there in e.g. video/voice conferences and in broadcast TV streams over IP networks. The protocols inlude
- Real-time Transport Control Protocol (RTCP)
- NetBIOS
- SOCKS
Layer 6 - Presentation Layer
The Presentation Layer is something that is quite often missing in the TCP/IP -model. Thus the usage is quite low, but the intention of this layer was to do
- Character-code translation
- Data
- Conversion
- Compression
- Encryption
Layer 7 - Application Layer
Now we come to the Application Layer which might be more familiar to the common people. This is what is often presented to users of computers using software:
- HTTP & HTTPS
- SMTP
- SSH
- FTP
- SNMP
Althought as computers are getting more consumer friendly the nasty technology acronyms are starting to fade out of the Graphical User Interface.
Making communication structured - The TCP/IP Model
The data networks we use to day follow the TCP/IP Model.
This is in examination throughout the course.
Layer 1/2 Link Layer
Here we use and learn Ethernet.
- Next week - Ethernet, VLANs and Switching
Layer 3 - Internet Layer
Here we use and learn IPv4 and IPv6.
Layer 4 - Transport Layer
Here we concentrate on TCP & UDP.
Layer 5/6/7 - Application Layer
Here are our applications such as HTTP(s) and SSH.
Continue on to the first exercise!
 E01 Making Your First Virtual Machine
E01 Making Your First Virtual Machine
Self-reflect the material with a small quiz?
![]() Data Networks Quiz - M01 Introduction to Data Networks
Data Networks Quiz - M01 Introduction to Data Networks
Back to the Schedule?
License
This course and its materials are written by Karo Saharinen and licenced by Attribution-NonCommercial-NoDerivatives 4.0 International (CC BY-NC-ND 4.0) license.